Allowlisting
Enables you to allow what you need, and block everything else, including ransomware.
Total Endpoint Control
Allowlisting has long been considered the gold standard in protecting businesses from known and unknown executables. Unlike antivirus, Allowlisting puts you in control over what software, scripts, executables, and libraries can run on your endpoints and servers.
This approach not only stops malicious software, but it also stops other unpermitted applications from running. This approach greatly minimizes cyber threats by stopping rogue applications from running on your network.


Block Unneccessary Executions
- Stop any application from running on your machine that is not a part of the allow list. This helps to mitigate and stop cyberattacks from happening across your device and network
- Add firewall-like application policies: A powerful firewall-like policy engine that allows you to permit, deny or restrict application access at a granular level
- Add Time-Based Policies: Permit access to applications for a specified amount of time. Automatically block the application after the policy has expired
- Keep up to date with Built-In Applications: ThreatLocker® automatically adds new hashes when application and system updates are released
Ringfencing™
Giving you complete control to help you manage your applications and better protect your endpoints.
Introducing Ringfencing™
Controlling what software can run should be the first line of defense when it comes to better protecting yourself against malicious software. Ringfencing™ adds a second line of defense for applications that are permitted. First, by defining how applications can interact with each other, and secondly, by controlling what resources applications can access, such as networks, files, and registries. Ringfencing™ is an invaluable tool in the fight against fileless malware and software exploits.

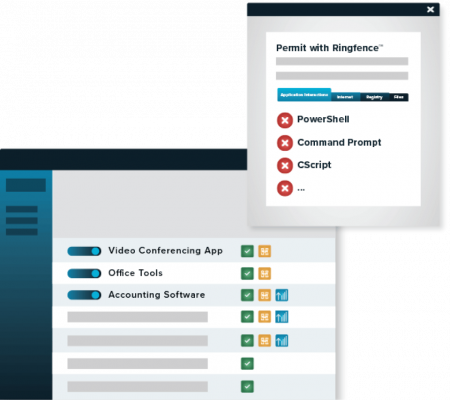
Protect Your Data From Malicious Behavior
- Stop fileless malware and limit damage from application exploits
- Define how applications integrate with other applications
- Stop applications from interacting with other applications, network resources, registry keys, files, and more
- Stop applications from interacting with built-in tools such as PowerShell, Command Prompt and RunDLL
- Stop built-in tools from accessing your file shares
Storage Control
Giving you complete control over your storage devices, including USBs and network shares.

ThreatLocker® Storage Control is an advanced storage control solution that protects information. We give you the tools to control the flow and access of data. You can choose what data can be accessed, or copied, and the applications, users, and computers that can access said data.
By using ThreatLocker®, you are in control of your file servers, USB drives, and your data. Most data protection programs on the market are butcher knife solutions to a problem that requires a scalpel.
Elevation Control
Run select applications as a local admin and remove local admin permissions without stopping productivity.

When it comes to adding extra layers of security to your cybersecurity stack, it’s important to always add a human layer. Users with admin access are often the weakest link across your network, so their movements must be monitored and tracked.
ThreatLocker Elevation Control provides an additional layer of security by giving IT administrators the power to remove local admin privileges from their users, whilst allowing them to run individual applications as an administrator.
Network Control
Cloud-managed endpoint and server firewall with dynamic ACLs to lockdown your endpoints and block unwanted network traffic.
Network Control allows for total control of inbound traffic to your protected devices. Using custom-built policies, you can allow granular access based on IP address or even specific keywords. Unlike a VPN that needs to connect through a central point, ThreatLocker Network Control is a simple connection between server and client.
ThreatLocker Network Control is built in a way that creates a seamless experience, enabling users to work as normal while eliminating the need for a solution, such as a VPN.
ThreatLocker Detect (Ops)
Detect and identify suspicious activity within your environment.
Don’t Let Vulnerabilities Go Unnoticed
ThreatLocker Detect looks for any anomalies that may make an environment vulnerable to a cyberattack. It analyzes data from ThreatLocker modules and notifies the admin if their system is using a version of software that’s known to have cyber vulnerabilities. Should a breach be attempted, ThreatLocker Detect can take steps to defend the system, such as taking automatic remediations, and Application Control will block any malicious payloads.

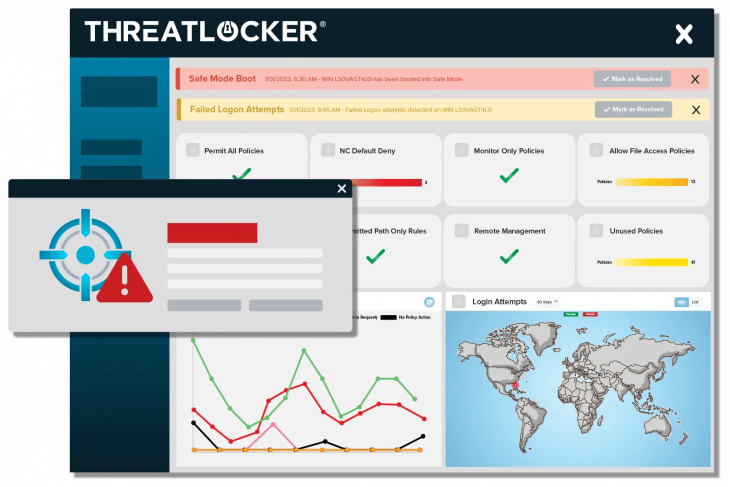
Key Capabilities of ThreatLocker Detect
Alert and Detect
Using industry-known indicators of compromise, ThreatLocker Detect can detect and alert IT professionals that their organization may be under an attempted attack based on customizable thresholds and notification methods.
Respond
Set policies to enable, disable, or create Application Control, Storage Control, or Network Control policies in response to specified observations.
Custom Threshold
Policies can be tailored to alert and respond differently based on the threat level to reduce alert fatigue.
Leverage Community Knowledge
IT admins can easily share their own ThreatLocker Detect policies or “shop” for vetted policies shared by their industry peers and the ThreatLocker team.
WHY THREATLOCKER?
Blocking Exploits of Known and Unknown Vulnerabilities
Remote access to your systems for outside users and partners is vital for today’s businesses, but it’s also a fertile avenue of attack for cybercriminals. ThreatLocker sees to it that even authorized visitors to your servers and systems can’t deliberately or unintentionally let malware in.
- Per User Limits: Eliminate the need to grant blanket access as ThreatLocker creates policies for organizations or unique users
- Protect Remote Assets: ThreatLocker is fully compatible with remote desktops and Citrix servers so employees can work securely from anywhere
- Control of Unknown Apps: ThreatLocker unobtrusively controls the applications of trusted visitors to prevent cybercriminals piggybacking in
Ransomware and other malicious software can copy or encrypt your files in a few minutes. ThreatLocker uses a more logical approach to stop viruses and malware from affecting your business. ThreatLocker Application Control uses a combination of default deny and Ringfencing to protect your business from known and unknown malware threats.
- Zero-Day Attacks: ThreatLocker protects against vulnerabilities that haven’t even been discovered yet
- Macro Viruses: Malware embedded in trusted programs like Office can’t overcome ThreatLocker Ringfencing
- Fileless Malware: Even malware that hides in memory can’t sneak in; if its code isn’t on the trusted list, it isn’t getting access
- Ransomware: Ringfencing lets you dictate how apps interact with data; if a program, ANY program, tries to encrypt data it isn’t authorized to, it will be blocked
It is important to know what is happening on your data storage devices at all times. Without that visibility, you risk these devices being left wide open to a cyber attack. ThreatLocker not only lets you track and control external data access (e.g., via the internet) but internal access as well. When your security team has complete visibility over your data storage, they’ll be able to block data theft before it happens.
- Control Physical Copying: With the right ThreatLocker Storage Control policies in place, a bad actor on your premises with a USB drive won’t be able to copy a thing
- Monitor Access: See who is accessing your files and when with detailed reports generated in real time by ThreatLocker
- Restrict Applications: Let only trusted apps access your data, as determined by your custom policies
With remote working on the rise, and the need for employees to be able to work anywhere, anytime, the need to track their computer activities is becoming increasingly important. ThreatLocker enables you to have visibility and control over the files and applications users are accessing on a day-to-day basis. With ThreatLocker you can:
- Track File Access: Get detailed, real-time reports on who accessed data and what they did with it
- Track Changes and Deletions: Thorough records for any file type let you see the complete history of your data
- Block Unauthorized Apps: ThreatLocker® custom policies let you block any apps you want, regardless of if they are malware or not
INDUSTRIES
BLOGS
Allowlisting vs. Blocklisting
Introduction
Allowlisting, formerly referred to as whitelisting, is akin to a security guard at a concert making sure the only people that go backstage with the band are on the VIP list. On the opposite end of the spectrum is blocklisting. Blocklisting, formerly called blacklisting, is equivalent to the security guard letting everyone backstage except for a few untrusted people on the deny list. If you were in the band, which method would make you feel more secure? How do you know that the only people that mean you harm are listed on the untrusted list?
For more information, please contact arjunp@bluechipit.com.au
RESOURCES
Awards & Recognition






Preventing Threats with Zero Trust Endpoint Security
< 6months
Payback on Investment with Enterprise Security
2M
Endpoints Protected
40k
Organizations Protected
$1.6M
Avg. Avoided Risk of Data Breach Costs
Success Stories
Meet a few of our customers and see how we’ve improved their security and operations.
Connect with Bluechip IT-Threatlocker Today!
Tap into our experienced product specialist and book a time to discuss your technological requirements. Let’s innovate the ever-so-changing world of technology together.











